Project overview¶
The aim of this project is to provide a platform for testing DRAM vulnerability to rowhammer attacks.
This suite can be run on real hardware (FPGAs) or in a simulation mode.
Read more about particular aspects of the framework in dedicated blog articles:
Tester suite architecture¶
This section provides an overview of the Rowhammer Tester suite architecture.
System architecture is presented in Fig. 1 below:
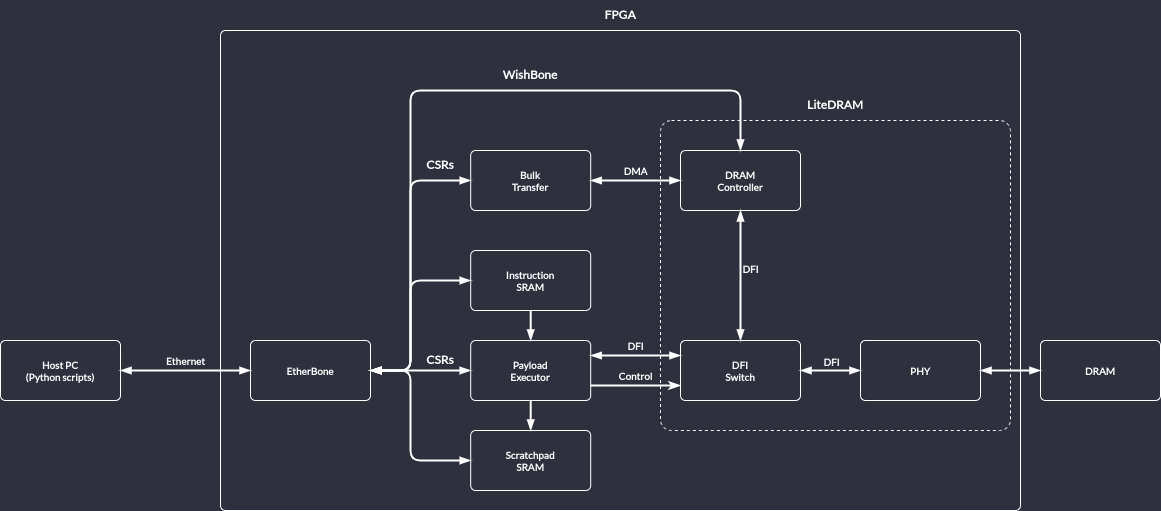
Fig. 1 Rowhammer Tester suite architecture¶
The DRAM is connected to LiteDRAM, which provides swappable PHYs and a DRAM controller implementation.
In the default bulk transfer mode, the LiteDRAM controller is connected to PHY and ensures correct DRAM traffic. Bulk transfers can be controlled using dedicated Control & Status Registers (CSRs) and use LiteDRAM DMA to ensure fast operation.
The Payload Executor allows executing a user-provided sequence of commands. It temporarily disconnects the DRAM controller from PHY; executes the instructions stored in the SRAM memory, translating them into DFI commands and finally reconnects the DRAM controller.
The application side consists of a set of Python scripts communicating with the FPGA using the LiteX EtherBone bridge.